Traditional approaches to identity and access management are struggling to keep up with the demands of seamless migration, diverse identity sources, varying workflows, and security.
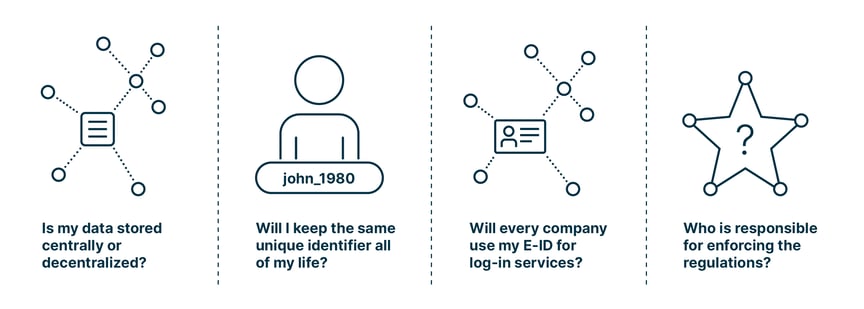
For users, digital identities come with a number of questions, such as: Will every company use my digital identity for log-in services? If my data is stored centrally, do I need to be concerned about paying a ransom when the database is hacked? Who is responsible for enforcing the regulations?
Enters the game-changer: identity fabric.
What is an identity fabric?
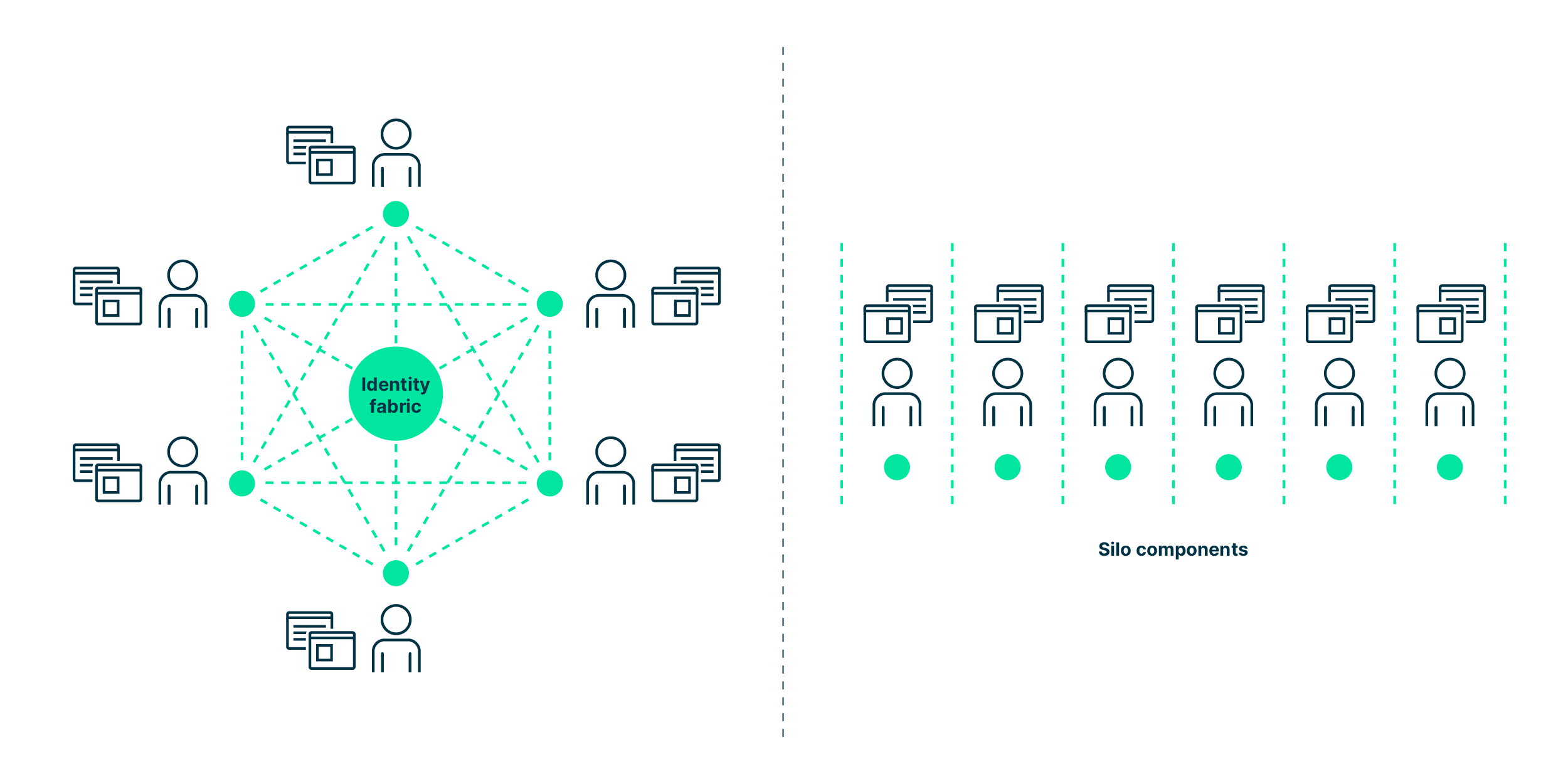
«Identity fabric» is a centralized approach for the management of digital identities. It provides a single view of all users and their access privileges. Plus, it addresses today’s challenges ensuring secure, seamless and controlled access to every service.
Identity fabrics come with distinctive features that set them apart from classical IAM solutions. This new vision and framework tackles today’s challenges ensuring controlled access to every service for any identity. By providing a single view of all users and their access privileges, it not only enables organizations to continuously assess their identity risks, but also ensures security for users.
Learn here from our Olivier Pallière, Principal Identity Architect, how to critically evaluate the integration of identity fabrics into your own business operations, precisely when it matters most. At the Global Cyber Conference Olivier Pallière will dive deeper into the topic.
1. Today, identity is probably the most critical element of security. Can you share your thoughts on the evolving landscape of digital identities and their impact on business operations?Digital identity is becoming the central element of any online infrastructure. Any business needs to identify its customers. What started as a way to personalize a user experience or save a basket has gradually become more regulated in accordance with law as its adoption grew. Identity spoofing or fraud are examples exploding online that drive the need for a much stronger stance to identity verification.
Since our lives increasingly happen online, it is crucial that what we see as «normal» in real life becomes our normal in the digital world – e.g., unfalsifiable id documents issued by a government, or traceability/accountability.
|
«Identity spoofing or fraud are examples exploding online that drive the need for a much stronger stance to identity verification.» Olivier Pallière |
|
2. How do you define identity fabric?
Identity fabric is a new vision and framework for the management of digital identities. It addresses today’s challenges ensuring secure, seamless and controlled access to every service for any identity – be it employees, partners, customers or things.
Identity fabric is a centralized approach that provides a single view of all users and their access privileges and thus identity security. This helps to simplify identity management and reduces the risk of unauthorized access. It is a methodology used to design logical IAM infrastructures.
3. As we just learned, the identity fabric approach treats identity types not as separate entities but as interwoven threads. How does this holistic approach contribute to more reliable risk assessment and decision-making within an organization?
Providing a single and comprehensive view of the identity landscape, identity fabrics help organizations to make more informed decisions, improving compliance.
It’s much easier to continually assess identity risks and to react to incidents with a central dashboard than to repeat the exercise within each individual silo component.
4. Identity fabrics facilitate the integration of various identity services and technologies. How does this integration empower CIOs and CISOs to effectively manage identities and access controls in a complex digital environment?
CIOs and CISOs benefit from the holistic view an identity fabric provides.
A key feature is the standard representation of identity data throughout the interwoven services. This representation greatly facilitates authentication, authorization, and accounting («AAA triad») and allows to efficiently address governance concerns.
For example, it makes working from home much easier from a security standpoint because it sets you free from perimetral security where people all have to be in the office and work with selected devices only.
5. Bruce Schneier famously stated: «If you think technology can solve your security problems, then you don't understand the problems and you don't understand the technology.» In the context of identity fabrics, to what extent do you agree with this statement, and how should organizations approach the adoption of new technologies?
I agree! Technology can be a very powerful tool for security but it is not a silver bullet. In the specific context of identity fabric, new risks it potentially introduces must be analyzed and mitigated through new security controls. Like for any other new technology, organizations should go by the motto «educate yourself, start small, be prepared to change».
A typical example: Believing that the identity fabric is a tool that can be installed in any company. It is key to understand that an identity fabric is unique to each company and requires a specific implementation.

6. How do you see the future of identity fabrics evolving, and what impact do you think it will have on the broader cybersecurity landscape?
Identity fabrics are well geared at tackling the challenges of the future as they offer many advantages over traditional identity architectures, such as security, flexibility, scalability, and cost effectiveness.
In particular the rise of cloud computing and the Internet of Things will drive the demand, as devices and users must continually be authenticated and authorized. Another driver is the ever increasing number of data privacy regulations which will require a central repository of identity data and security controls.
The cybersecurity landscape has changed considerably. Covid was a real catalyst: It made working from home a routine, with especially young people taking remote work for granted. Today, we see a paradigm shift. We no longer adapt to security, but security adapts to our behavior.
7. Identity fabric and zero trust are two different ways of managing business resources (one focusing on identity and the other on data). Is a single solution suitable for every organization?
No, identity fabric and zero trust are not mutually exclusive but rather complementary. The former provides a single view of all users and their privileges, thus reducing complexity, while the latter ensures no devices or user can be trusted, thus increasing security.
Not all organizations can implement this hybrid approach. Factors like the size of an organization or its complexity have an impact, as well as security requirements, technical expertise or budget.
8. A lot of data breaches happen because identity and access controls are insufficient, how can organizations enable user access without compromising security?
A report from Verizon states that 81% of data breaches happen due to weak or stolen credentials. A simple yet effective method is the adoption of multifactor authentication, such as FIDO2, using biometrics identifiers.
In addition to technical measures, there is also a compliance and governance aspect. Enforcing a least privilege access policy also reduces the risks by preventing unauthorized access by default. Plus, access must regularly be assessed and recertified.
As we just learned, an identity fabric comes with numerous benefits, such as a holistic view of all users and privileges, easier risk assessment, or secure, seamless and controlled access to every service for any identity. Offering this many advantages over traditional identity architectures, identity fabrics are the technology of choice to prepare for future challenges.
After all, co-boosted by Covid, the cybersecurity landscape has changed considerably. Today, a paradigm shift is taking place: We no longer adapt to security, but security adapts to our behavior.
What better reason could there be for you to fortify your operations in the face of the limitations posed by traditional IAM solutions?







