- On this page
- What is an identity and access management strategy?
- How do you develop an IAM strategy?
- What are common IAM strategy challenges?
- IAM strategy: How to improve it
- Identity fabric: The ultimate booster for IAM
- Six indicators you need to improve your IAM strategy
- Play it safe – go for the big picture!
In 2024, digital identity verification has become an integral part of our online activities, from simple shoe purchases to complex business operations. However, traditional approaches to identity and access management are struggling to keep up with the demands of seamless migration, diverse identity sources, and varying workflows. High time for organizations to introduce a trailblazing solution: identity fabrics.
In this article, we – Christian Egli, IAM architect with SBB, and Olivier Pallière, Principal Identity Architect with Adnovum – will unveil the key indicators about when and how to adopt an identity fabric for your company. You cannot only expect an exploration of the motivations, challenges, and advantages that accompany an identity fabric. You will also gain a solid understanding of the distinctive features that set identity fabrics apart from classical IAM solutions.
What is an identity and access management strategy?
An identity and access management (IAM) strategy is a structured framework of policies, processes, and technologies that organizations use to manage digital identities and their access to company assets.
In today’s increasingly digital world, IAM has become a critical part of an organization’s security posture, as it helps protect sensitive data and systems from unauthorized access. After all, compromised user credentials are known to be the most common targets of attackers.
An IAM strategy consists of the following key components, or pillars:
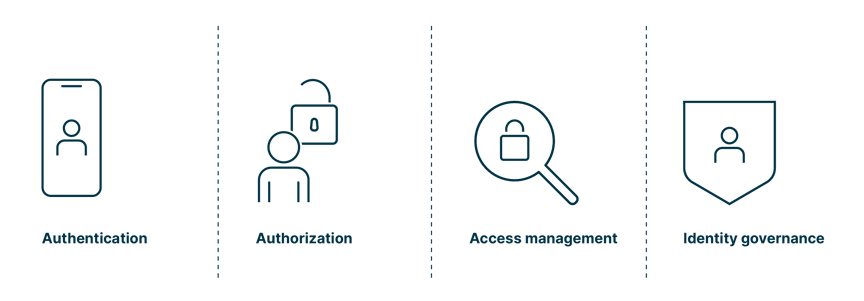
- Authentication
Authentication is the process of verifying an identity, typically using credentials such as username and password. Today, it is enhanced with multi-factor authentication. - Authorization
Authorization is the process of granting users access to whatever resources needed based on their job roles and responsibilities. - Access management
Access management describes the ongoing process of monitoring and managing user permissions. While access management includes granting and revoking access, it also puts a focus on auditing user activity to identify and mitigate any potential security risks. - Identity governance
Identity governance means managing and maintaining identities throughout their life cycle, from onboarding to offboarding. This includes the provisioning and deprovisioning of target accounts, managing users’ attributes and ensuring that user information in the IAM system is always accurate and up-to-date.
An IAM strategy brings significant benefits such as reducing the risk of data breaches and thus helping improve compliance, efficiency through automation and ultimately global productivity.
How do you develop an IAM strategy?
Like all enterprise architecture elements, developing an IAM strategy is an iterative process. It should comprise the following steps:

- Define the IAM objectives
Define the goals that the company wants to achieve as well as specific requirements in terms of compliance and security and how they should fit within the organization’s overall security posture and risk management framework. - Compile a thorough inventory of all the assets
To do so, identify your assets, applications, services, and datastores. - Identify your users
Determine who needs to access the identified assets and categorize them based on roles and responsibilities. The users are not limited to your employees or one kind of person. It can be your staff, partners, external contributors, or customers, each with different needs. Plus, it can be machine identities. Those represent a big part of the identity data used throughout a mesh architecture application, where services need to securely communicate. - Define IAM capabilities
Based on your users and assets landscape, define the enterprise capabilities that you need to achieve the set objectives. - Define an implementation plan
The plan will serve as a roadmap to integrate the technologies that match your requirements. - Implement the strategy
- Evaluate, adapt, repeat
What are common IAM strategy challenges?
|
«IAM has become a critical element of any business, leading to new security challenges. In addition to security, topics such as governance, audit, scalability, monitoring, and integration must be infused in an IAM strategy.» Olivier Pallière |
|
We’ve seen that IAM has become a critical element of any business, as we are moving away from the traditional IT security where it was possible and normal to rely on firewalls and dedicated security components. Today most every service is out in the open, i.e., publicly available. This is true for customer applications but also becoming a reality for a lot of enterprise clients using cloud services like Microsoft Office 365, Trello, or a Miro Board. While firewalls are still used to protect the infrastructure running those services, the apps themselves are not protected.
As a result, an IAM strategy has to address many new use cases and threats, leading to new security challenges. However, security is just one area of an IAM strategy. Governance, audit, scalability, monitoring, and integration are a non-exhaustive list of important topics that must be infused in an IAM strategy. Depending on what is deemed a «must» requirement in the IAM objectives and capabilities, it is possible to classify those challenges.
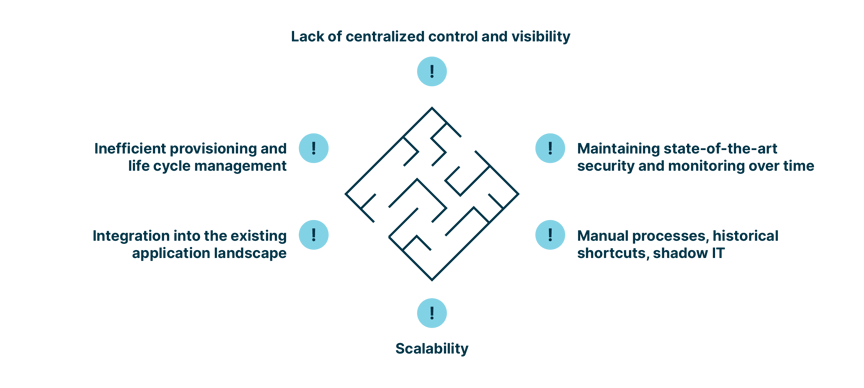
Here are a few examples we’ve seen in numerous real projects:
- Lack of centralized control and visibility
It is difficult to visualize what is happening in the IAM landscape, to identify incidents and the health status of the IAM functions – in particular to do that in one place. Many different actors in an organization must collaborate to provide a clear overview of an IAM architecture. - Inefficient provisioning and life cycle management
IAM automates lengthy and complex processes of user account creation and the management of their profiles. A user being onboarded means they will get a number of accounts in subsystems to work, from accessing the buildings to logging in to their workstation. However, some accesses and accounts do not work on day one in the new organization. Another issue are accounts and permissions that linger around after a user or a service account is no longer part of the organization or needed. - Integration into the existing application landscape
Often a lot of legacy applications are used in an organization. Integrating those into the IAM strategy presents challenges as interfaces might be unavailable or unable to use standard protocols and APIs. - Maintaining state-of-the-art security and monitoring over time
We said that defining an IAM strategy is an iterative process. It should continuously be evaluated, monitored and adapted to the current trends in terms of attack and risk mitigation, for example. - Manual processes, historical shortcuts, shadow IT
You can define the best strategy and implement it using state-of-the-art technology – if it is too cumbersome, complicated, counterproductive, or simply annoying, there is a good chance that the process you establish will be bypassed over time. We all have experienced shadow IT: for example, staff installing their own gateway or Wifi to bypass the proxy. - Scalability
Scalability, or rather the lack thereof, is another major challenge of an IAM strategy as it can jeopardize an implementation.
IAM strategy: How to improve it
It primarily requires a mindset change to introduce a holistic approach to IAM as a central element of a security posture. When you do, focus on:
- comprehensive identity governance
- implementing multi-factor authentication
- conducting regular audits
- utilizing role-based access control
- educating users on security practices
- integration with the IT ecosystem
- automating processes
- staying updated on security threats
- having an incident response plan
- collaborating with stakeholders to align IAM with organizational goals
Collaboration between the different actors within an organization is key to ensure scalability and address potential pitfalls. One of them is shadow IT, i.e., the use of unauthorized or unapproved applications, software, or technology solutions, which can result in security and compliance risks. Such unmanaged technologies might not adhere to the organization’s security standards, potentially leading to data breaches.
A current trend used to significantly improve an IAM strategy and address modern challenges is identity fabric.
Identity fabric: The ultimate booster for IAM
Identity fabric, at its core, is a cutting-edge concept and methodology revolutionizing IAM. Functioning as a high-level architectural framework within IAM, identity fabric takes a centralized approach to deliver a comprehensive overview of all users and their access privileges. This unified perspective not only simplifies identity management but also bolsters identity security by minimizing the potential for unauthorized access. Essentially, identity fabric enables the strategic design of logical IAM infrastructures for enhanced efficiency and security.
Modern applications are no longer big monolithic blocks but rather relying on a multitude of micro services organized in a service mesh working together. And each of those services needs access to identity data. This should be represented in a unified way, ensuring consistency throughout an organization and allowing for centralized visualization and identity management.
The following table compares traditional IAM with the identity fabric concept:
| Traditional IAM | Identity fabric | |
|
Decentralized |
Centralized |
|
|
History-based view |
Holistic up-to-date view |
|
|
Individual risk assessment |
Overall risk assessment |
|
|
Silo-based |
Collaborative |
|
How to shift from IAM to identity fabric
Shifting from a traditional IAM to an identity fabric is a strategic move for your organization. Here is a breakdown of the 5-step process to get started:
- Step: Assessment
- Current IAM state: Evaluate your existing IAM system's functionalities, limitations, and how it currently integrates with your IT landscape.
- Identity fabric needs: Identify your business goals for adopting an identity fabric. Consider factors like the variety of identities (employees, customers, partners), access needs across applications, and desired security posture.
- Step: Planning and design
- Gap analysis: Analyze the gap between your current IAM capabilities and the functionalities offered by an identity fabric.
- Phased migration: Plan a phased migration approach that minimizes disruption. You can potentially keep core functionalities on the traditional IAM system while migrating specific areas to the identity fabric.
- Step: Implementation
- Identity fabric selection: Research and evaluate different identity fabric solutions based on your needs, budget, and technical expertise.
- Integration and configuration: Integrate the identity fabric with your existing IT infrastructure and configure access controls and workflows.
- Step: Deployment and testing
- Pilot testing: Conduct pilot testing in a controlled environment to ensure smooth operation before full deployment.
- User training: Train users and IT staff on the new identity fabric system and its functionalities.
- Step: Restart at step 1
- Go back to assessment and continually monitor, measure, and adapt the identity fabric.
Six indicators you need to improve your IAM strategy
|
«Improving your IAM is about the big picture, seamless integration, and strategy. There are specific indicators that tell you when it’s time to act: e.g., the need for a central policy layer and global dashboard, an inconsistent access model, or overloaded IAM teams.» Christian Egli |
|
Drawing from my personal experience as the IAM architect at SBB, I have identified six key indicators that have emerged as the crucial elements of identity fabric. In the following sections I am going to elaborate on each of these indicators:
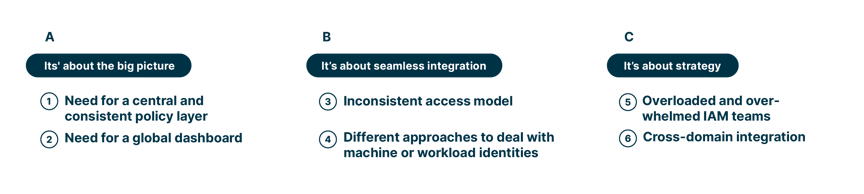
- It's about the BIG PICTURE
Indicator 1: Need for a central and consistent policy layerRecently, a senior cyber security executive asked me to explain all the access policies in our IAM landscape within a 10-minute appointment. I was overwhelmed by the request as we have numerous policies covering various aspects such as customer and workforce identities, authentication, credential management, and role-based and attribute-based access control. It was impossible to cover everything in such a short time.
Despite my initial attempt to brush off the request, I recognized the importance of his question. Managing policies across various building blocks necessitates an overarching central policy layer that can be centrally controlled and decentrally enforced. It's not just about individual policies; it's about the bigger picture.
Therefore, I recommend asking your responsible IAM staff to provide a concise explanation of IAM policies within 10 minutes. If they struggle to do so, it may be an indication that adopting identity fabric patterns is necessary.
Indicator 2: Need for a global dashboard
Let's discuss privileged access and its importance, including critical accounts like Global Admin and root. When managing IAM, we often focus solely on our IAM landscape. However, when it comes to privileged access, we must consider our cloud environments, which host numerous Kubernetes clusters and a significant portion of our applications. Engineers administering these infrastructures also wield privileged access. And while our cloud environments are automated through pipelines, we still need individuals with privileged access to our CI/CD environments.
Merely controlling privileged access in individual subsystems is inadequate. We need a centralized dashboard to visualize gaps, overlaps, and identify overprivileged accounts. Ideally, this dashboard would generate heatmaps and offer recommendations to address these issues efficiently.
- It’s about SEAMLESS INTEGRATION
Now let's delve into integration. While Lego bricks seamlessly integrate across generations, our IAM infrastructure's building blocks aren't always as compatible.Indicator 3: Inconsistent access model
For legacy applications, partners from other companies are required to use an SBB account. However, as we introduce new SBB business applications, these partners can use their own company accounts with single sign-on through identity federation. This mix of accounts highlights the inconsistency in our access model, which partners notice even from the outside.
Indicator 4: Different approaches to deal with machine or workload identities
Another indicator of incomplete integration is the varied approaches we have for handling machine or workload identities. We currently obtain certificates from different PKIs, while OAuth2 is increasingly used through our API management platform. This lack of a clear decision-making basis for developers and architects, along with the difficulty for IAM and security managers to maintain an overview, further demonstrates the need for improved integration.By addressing these indicators, we can work towards achieving a more seamless and unified IAM infrastructure.
- It’s about STRATEGY
Indicator 5: Overloaded and overwhelmed IAM teams
An important indicator that you should adopt an identity fabric is the workload of your IAM team. The ones at SBB had been suffering from a very high workload for years. This is why we invested heavily in automation, from self-services to automated governance processes, to optimize our IAM resources and efficiency.A key point for us was the transformation of our IAM team from pure operations to DevOps teams and assigning an increasing number of software developers to it. Software developers come with a different mindset that is essential for adopting an identity fabric: It's more than just problem-solving. It’s about strategic development, automation, and implementing all the integration tasks mentioned in indicators 3 and 4.
Indicator 6: Cross-domain integration
Identity and access management is extending its reach into various other domains, as the graphic below shows. For instance: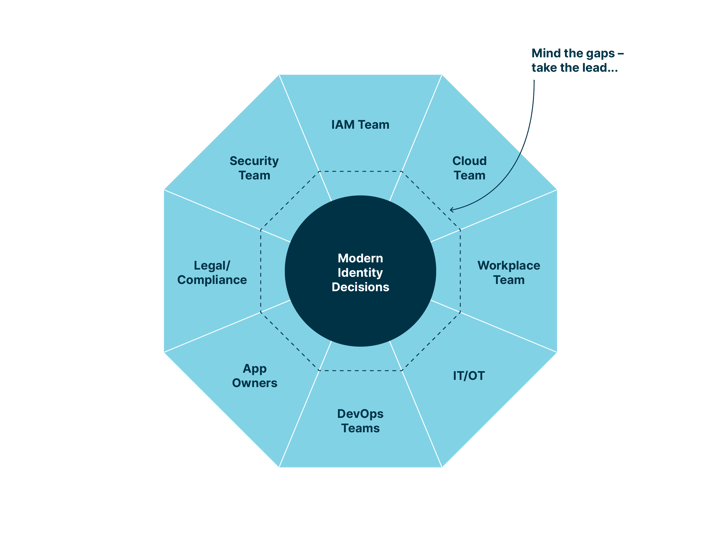
- Privileged access management (PAM) has become a concern not only for IAM but also for teams responsible for central IT infrastructure such as cloud teams.
- To enforce fine-grained access, we rely on signals from employees' work devices like laptops and mobile phones. This collaboration with our Workplace team, which handles device management and deployment, is crucial.
- Effective threat detection and response require close collaboration with our Security teams and others.
It is important to note that these teams have different priorities, with information security not being their primary focus. This is where the IAM architect plays a vital role and takes on the responsibility. Adopting an identity fabric helps identify and bridge organizational gaps, enabling a seamless and secure IAM experience.
Play it safe – go for the big picture!
Digital identities are here to stay. We just learned what the pillars and the challenges of an IAM strategy are and how to develop such a strategy. Yet, in this increasingly digital world this is not enough to keep your organization safe. If the 6 indicators described above reflect your organization’s current state, you definitely need to delve into the topic of identity fabrics. Remember: identity fabrics stand for a holistic view of all users and privileges, easier risk assessment, as well as secure, seamless and controlled access to every service for any identity.
Identity fabrics are the technology of choice to prepare for future challenges.
Written by

Olivier Pallière
Principal IAM Engineer, Adnovum

Christian Egli
IAM Architect, SBB





