- On this page
- What is a cybersecurity culture?
- Why is cybersecurity culture so important?
- What is a good cybersecurity culture?
- Who is responsible for cybersecurity culture at Swiss companies?
- How do you build a cybersecurity culture at your company?
- Types of common cyberattacks and how to detect them
- Cybersecurity culture success stories: 5 Swiss companies to learn from
- Your employees are your most valuable asset – more than ever
Cyberattacks on companies remain on the rise. In Q3 2024 alone they increased by 75% worldwide, and even by 114% in Switzerland compared to Q3 2023. No matter the size, industry, number of assets, or employees – any business can be a target. Someone falls victim to a cyberattack roughly once every 11 seconds.
With the increased use of new technologies, such as advanced software applications, cloud computing, and the Internet of Things (IoT), organizations are setting up a large attack surface. How to counter the challenge and protect your assets?
It’s the people that make an organization secure. This is why they need the right mindset and the necessary knowledge to secure your corporate assets.
The solution is a solid cybersecurity culture. We will show you what it takes and how to establish a healthy cybersecurity culture.
What is a cybersecurity culture?
 A cybersecurity culture refers to the collective mindset, behavior, and practices of individuals within an organization regarding their approach to cybersecurity. It is about fostering an environment where every single person – from top management to employees at all levels – understands the importance of cybersecurity. Plus, where every individual actively helps protect the organization's digital assets and information from cyberthreats.
A cybersecurity culture refers to the collective mindset, behavior, and practices of individuals within an organization regarding their approach to cybersecurity. It is about fostering an environment where every single person – from top management to employees at all levels – understands the importance of cybersecurity. Plus, where every individual actively helps protect the organization's digital assets and information from cyberthreats.
A strong cybersecurity culture goes beyond just having a set of rules or policies in place. It involves creating a sense of shared responsibility and awareness throughout the organization.
This shared responsibility is best supported by strong automated assistance, e.g., an Outlook feature warning about a phishing attempt, based on the Human-Centered Security (HCS) approach. In addition, it should be strengthened by providing security awareness trainings, e.g., workshops where employees learn how to recognize a phishing attempt, how to avoid the injection of malware, or why strong passwords are key.
The different levels of culture
To define «culture», it is important to differentiate between the levels at which it manifests itself. These levels range from the very tangible manifestations that one can see and feel, to the deeply embedded, unconscious, basic assumptions that can be defined as the essence of culture. In between are different beliefs that members of the culture use to represent the culture to themselves and to others.
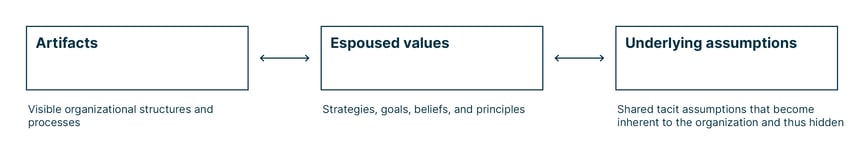
Artifacts
Artifacts are the directly visible things you can observe, see, and feel in your organization, such as structures and processes. This first level reflects «the way we do things around here».
For example, an information security policy document is a formal artifact that defines how information security is to be handled within your organization.
From the visible artifacts, you can conclude a lot about culture, especially the cybersecurity culture. Take a few minutes to figure out the visible artifacts of your company's cybersecurity program. Is it hard to find any? Do you already know all the documents and where to find them? Do all of the employees know about them? If not, there is probably no cybersecurity culture established in your organization.
Espoused values
Espoused values are the official statements of your organization concerning strategies, goals, values, beliefs, and principles. Such a statement can be a commitment to respect the privacy of users concerning their data. Other sources of values, beliefs, and principles are vision or mission statements.
Underlying assumptions
Shared tacit assumptions are the hidden layer of any organizational culture. They are the reason why cultures cannot just be changed by creating and publishing a new policy document. These assumptions are built over time and reflect an organization's cumulative experience and knowledge of how to succeed.
For example, in a market where efficiency and fast time to market are critical, employees build strategies to succeed in this market. Over time, these strategies are so inherent to the organization that they become unconscious and hidden. Because they are an integral part of the company's past success, it is so hard to work against them if, for example, the external environment changes like with the introduction of the GDPR in 2018.
Why is cybersecurity culture so important?
A strong cybersecurity culture helps protect an organization’s most important asset: its data. Unlike physical assets such as equipment, buildings, and even people, data is difficult to replace. Most organizations spend years to acquire data – and many may go bankrupt when they lose it.
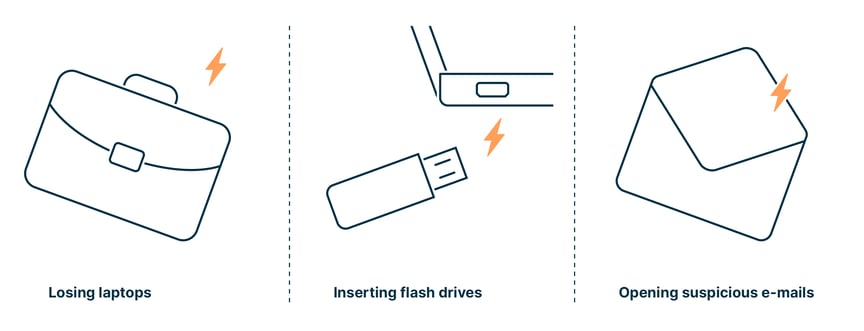
It is therefore key for organizations to protect their data assets at all levels. The good news: Simple security standards that all employees follow can address most security issues, because human error or behavior causes 90% of all cyberattacks. Employees losing their laptops, inserting flash drives into their computers, or opening suspicious e-mails compromise more organizations than malicious hacks from external attackers.
Thus, it is not enough to spend a large amount of money on hardware and software such as firewalls, virus protection and physical barriers. Organizations need to invest in their employees:
- by providing them with automated tools and detection helps and making them more familiar with Human-Centered Security, and
- by organizing training as well as building and enforcing standards that provide protection from human behavior.
What is a good cybersecurity culture?
|
«The best security is the kind you don't see and that allows employees to be productive.» Michel Sahli |
|
A good cybersecurity culture is essential for any organization to effectively protect its assets, data, and systems from cyberthreats. It involves fostering a collective awareness and commitment to cybersecurity best practices among all members of the organization. Here are some key elements that contribute to a strong cybersecurity culture:
Leadership and management commitment
A good cybersecurity culture starts at the top. Leaders and management must prioritize cybersecurity, allocate resources, and demonstrate their commitment to security initiatives. They should lead by example.
Responsibility and accountability
Everyone in the organization should understand their responsibility for cybersecurity. Encouraging a sense of ownership and accountability for security helps create a more vigilant workforce.
Employee awareness and training
Regular cybersecurity awareness training for all employees is crucial. It helps them understand the importance of cybersecurity, recognize common threats (such as phishing attacks), and know how to respond appropriately to incidents.
Encouraging reporting of security incidents
Creating a culture that encourages employees to report suspicious activities or potential security incidents without fear of reprisal is crucial. This early warning system helps in mitigating potential threats.
Incident response plan
Having a well-documented response plan enables a swift and coordinated response to cybersecurity incidents. Employees should be aware of the plan and their roles during such events.
Clear security policies and procedures
Organizations should establish comprehensive and well-defined security policies and procedures that align with industry best practices. These policies should cover topics such as data handling, password management, and acceptable use of technology.
Data protection and privacy
A strong cybersecurity culture also involves respecting data protection and privacy regulations and safeguarding sensitive information.
Continuous improvement
Cybersecurity is an ever-evolving field. Encourage a culture of continuous improvement by learning from security incidents and staying informed about the latest threats and best practices.
By promoting these principles, organizations can build a strong cybersecurity culture that reinforces their resilience against cyberthreats and ultimately protects their business, customers, and stakeholders.
Who is responsible for cybersecurity culture at Swiss companies?

A culture of sustainable cybersecurity requires everyone in the organization to assume responsibility by knowing and following the security policies – from senior executives to stakeholder advisers and employees.
Roles and responsibilities in organizations of different sizes
As we just learned, establishing a cybersecurity culture in an organization is a collective effort that involves multiple stakeholders. The following groups and roles typically play key roles in fostering a strong cybersecurity culture:
In general and in large-sized businesses (250+ employees)
Leadership and management
Executives, senior management, and board members have a critical role in setting the tone for cybersecurity within the organization. Their commitment to cybersecurity initiatives, resource allocation, and communication of the importance of security sets the foundation for the entire culture.
Chief Information Security Officer (CISO)
The CISO or equivalent role is responsible for the overall cybersecurity strategy and program within the organization. They lead efforts to identify risks, implement security measures, and ensure compliance with relevant regulations. The CISO plays a central role in shaping the organization's cybersecurity culture.
Human resources
HR departments play a role in ensuring that employees are educated about cybersecurity policies and practices. They can facilitate training sessions, create policies for secure onboarding and offboarding of employees, and incorporate cybersecurity awareness into the organization's training and development programs.
IT teams
IT teams implement technical security measures, manage network and system security, and respond to security incidents. They contribute to the cybersecurity culture by ensuring that employees have the tools and systems needed to work securely and by enforcing security policies.
Communications and training teams
These teams are responsible for creating and delivering cybersecurity awareness training programs for employees. They ensure that employees understand the risks, know how to recognize threats like phishing attacks, and are aware of the proper security practices.
Employees
Every employee within the organization is a critical component of the cybersecurity culture. They need to be engaged, educated, and motivated to follow security best practices. Encouraging a sense of personal responsibility for cybersecurity helps create a culture of vigilance.
Internal auditors and compliance teams
These teams assess the organization's adherence to security policies and regulatory requirements. They help identify areas of improvement and ensure that the cybersecurity culture is being implemented effectively.
Legal and risk management
Legal and risk management teams collaborate to ensure that cybersecurity practices align with legal and regulatory requirements. They also assess potential legal and financial risks associated with security breaches.
Small and medium-sized businesses (10–249 employes)
In smaller organizations, responsibility for cybersecurity is typically distributed among various roles and individuals, as their resources and structure may not allow for an IT, a legal, and an HR or even dedicated cybersecurity team. Close cooperation is therefore particularly important.
Key differences in cybersecurity culture between small/medium and large organizations
The cybersecurity culture can differ significantly between small and large businesses due to various factors, including resources, organizational structure, risk tolerance, and regulatory requirements. Here are some key differences:|
|
Small and medium-sized business |
Large business |
|
Resources |
|
|
|
Organizational structure |
|
|
| Risk tolerance |
|
|
|
Organizational structure |
|
|
|
Employee awareness and training |
|
|
|
Vendor and supply chain management |
|
|
|
Communication and collaboration |
|
|
|
Incident response |
|
|
|
Technology infrastructure |
|
|
|
Cultural factors |
|
|
Of course, these differences are generalizations and there can be significant variation within both small and large businesses. Additionally, as the cybersecurity landscape evolves, businesses of all sizes are becoming increasingly aware of the importance of strong cybersecurity practices to protect their assets, reputation, and customer trust.
How do you build a cybersecurity culture at your company?
Having a sustainable cybersecurity culture is more than just a one-time event – it’s a life cycle that will generate returns forever.
The investment will certainly pay off: A cybersecurity culture empowers organizations to guide the behavior of employees when interacting with information assets, thus making them understand and avoid activities that may jeopardize the organization and their assets.
Here are five down-to-earth tips on how to build a cybersecurity culture:
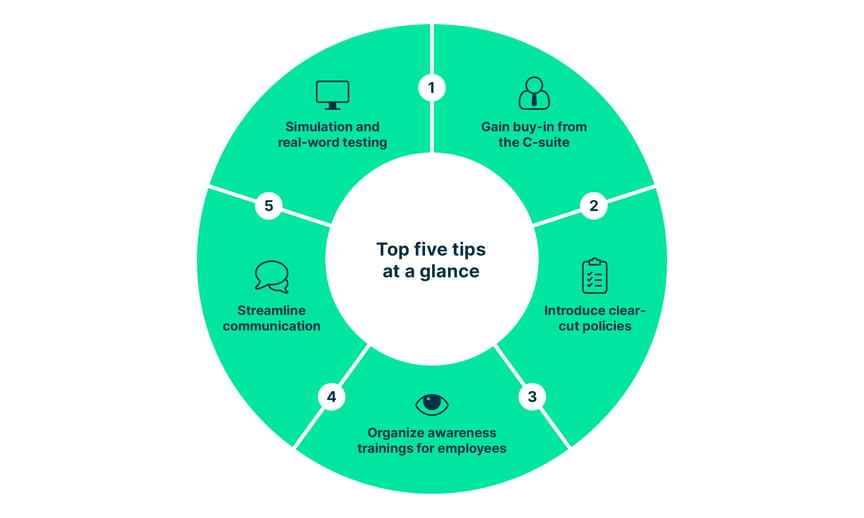
1. Gain cybersecurity buy-in the C-suite
The commitment of the leadership team is crucial to successfully establish a cybersecurity culture and bring about real change. More precisely: a leadership team which proactively manages and promotes cybersecurity and embraces security as part of the company-wide culture.
The six principles of cybersecurity management
For a company to excel in its cybersecurity initiatives, a structured approach is imperative. The foundation of this structure lies in a set of guiding principles, each essential in its own right and collectively forming a robust cybersecurity strategy. The following six principles serve as guidelines:
- Treating cybersecurity as a company-wide module of risk management
Executives must champion cybersecurity across the entire organization, ensuring that it integrates seamlessly into broader risk management strategies. Their role is pivotal in identifying potential threats and acting before they materialize. - Understanding the legal impact of cyber risks
Awareness of the legal ramifications of cyber incidents is crucial. The leadership team should be equipped with knowledge about potential legal consequences to build a comprehensive defense strategy. - Ensuring access to cybersecurity expertise and regular exchange
Securing the company necessitates a significant investment in expertise. This includes not only funding but also dedicating time, ensuring the availability of skilled personnel and up-to-date technology, and visiting workshops. These resources aid in both internal training and fostering external collaborations. - Implementing the suitable framework and resources for cyber risk management
Leadership must adopt a well-structured framework tailored to the company's specific threats and vulnerabilities. In Switzerland, this can include the ISO/IEC 27001 standard, the NIST Cybersecurity Framework, and the BSI IT-Grundschutz. Ensuring the proper resources in terms of personnel and technology is also paramount. - Analyzing the risk and defining the risk tolerance based on business goals and strategies
Each company has unique thresholds when it comes to risk. Leadership must identify these boundaries, ensuring that cybersecurity strategies align with broader business objectives and the company's comfort with risk. - Promoting company-wide collaboration and exchange of best practices
Cybersecurity thrives on collaboration. Encouraging active cooperation both within and outside the organization is essential. This involves not only sharing insights and best practices among departments but also supporting external collaborations through events like workshops. Emphasizing clear communication and a culture of continuous learning keeps the organization united and vigilant against threats.
2. Introduce clear-cut cybersecurity policies that foster accountability
A workplace with strict security policies and procedures in place is always more secure, efficient, and productive – provided every single employee understands and implements them on a daily basis. This can be encouraged by fostering accountability.
The policy needs to include the following security requirements:
- Usage of hardware, software, data media and data which is not provided by the employer is not permitted (e.g., external USB data storage devices)
- Usage of organization-owned software or data on IT devices that are not provided by a third party or an approved supplier (e.g., usage on personal devices) is not permitted
- Usage of company-owned software or data on storage media (e.g., file or cloud services) that are not approved is not permitted
In addition, the security policy needs to address the following questions:
- Purpose
What topics does the policy cover? Does it cover expected behavior when using computers and mobile devices? - Context
Does the security policy include content on new technologies and practices? - Strictness
Does the policy prohibit certain behaviors, for example, the use of external USB data storage devices? - Compliance
Does the organization's security policy reflect good practices? - Accountability and consequences
Does violation of the security policy include the possibility of suspension or termination of employment?
Accountability is key
Experience shows that the basis of practical policies is accountability. There are two ways to foster it: by rewarding security efforts and/or sanctioning violations.
- Rewarding efforts
Once someone successfully completes a mandatory security program, give them a «high five» or something more substantial, such as a voucher for a dinner. They will be quick to tell their colleagues – and they will quickly jump into training. This is one more reason to make security enjoyable, for example, by starting the training session with a game.
You can even include security as a career choice and offer employees the opportunity to grow into a dedicated security role.
- Sanctioning violations
Record, review, and adequately sanction violations with no consideration of the violating party's rank or position. Encourage employees to inform their superior about violations and make sure managers take such information seriously. The key to adequately dealing with violations is a trustful work environment.
3. Organize cybersecurity awareness trainings for employees
The best way to firmly establish a cybersecurity culture is to raise employees’ awareness of the serious implications of cyberattacks. This will help them understand why they must follow security policies in their daily work.
Cybersecurity trainings are effective in supporting this process. An engaging way is role-playing games in which employees go through security-related issues and find ways to solve them in alignment with security policies.
Important: Package security awareness trainings so that each target audience receives the relevant training. Consider their department knowledge, responsibility level, as well as the data they access and tools they use. For example, employees who do not have direct access to databases systems do not require a training related to database security. The frequency depends on the organization's needs and employees' learning curve.
From a high-level view, the content of a training needs to be:

-
Understandable
Use hands-on and easy to understand content
-
Relevant
For example, a security training on cryptography would be irrelevant to HR
-
Actionable
As a result of the training, all employees should know what to do in common situations. For example, employees who are on travel or work from home and use their mobile devices should be aware of the following:
-
Shoulder surfing (use privacy filters)
-
Only use public networks with VPN
-
No confidential calls in public areas
-
Do not dispose of company documents in household waste
-
- Memorable
The content should enable employees to memorize and practice skills, for example, by using a secure password and responding to e-mails or interacting with people outside the organization.
By developing appropriate knowledge and a habit of learning security best practices on a regular basis, employees will be able to detect and mitigate a security incident effectively. To be on the even safer side, make sure to also assist employees with technical tools and detection helps.
4. Streamline communication on cybersecurity
Communication is vital when it comes to effective threat handling and mitigation. Make channels of communication clear, simple, and accessible for everyone so that any suspicious activity can be reported to the relevant team without hesitation. Never criticize your employees for communicating an incident that may turn out not to be an important threat. If you do, this could discourage them from communicating any malicious activity in the future.
Key aspects of easy communication
The most important aspect is continuous communication. It is about reinforcing processes for security-related notifications and regularly communicating progress. Both employees and management should discuss what is going well and what could be improved. A team-oriented attitude increases the feeling that everyone is working towards the same goal.
|
Dos |
Don'ts |
|
|
|
|
|
|
|
5. Cyberattack simulation and real-word testing
Companies around the globe are testing their employees by using different tricking and phishing techniques. This allows them to see how well employees respond to cybersecurity attacks and what steps they take to mitigate the issue. Testing with some real-world cyberattack simulations can uncover the weak areas of your employees and will help you improve them.
As regards the infrastructure, it is key to systematically conduct penetration tests to identify how vulnerable your organization’s systems are. A solid risk awareness encourages project managers to do a penetration test before every major release of new software. To formalize the testing requirement, a security policy for projects can be put in place. Based on the results, security measures should be implemented to protect the IT infrastructure in the event of an actual attack.
Types of common cyberattacks and how to detect them
Ransomware and malware
With a ransomware attack, hackers gain access to an organization’s network. They steal and/or encrypt data, destroy backups, and implement remote access. As encrypted data is useless, the hackers demand a ransom for providing the decryption key. To increase pressure, they often threaten to publish sensitive data.
Detecting a ransomware or malware attack early is crucial to minimizing the damage and preventing the spread of the malicious software. Here are some steps employees can take to help detect such attacks:
- Stay alert for unusual behavior
If something seems off or different from the usual, it might be a sign of a ransomware attack. - Be cautious with e-mails and attachments
Be skeptical of unsolicited e-mails and verify the sender's identity before opening attachments or clicking on links. Look for suspicious e-mail addresses, misspellings, or unusual language in e-mails. - Be vigilant to file encryption
Keep an eye out for files with strange extensions, such as «.encrypted» or «.locked». Also, if you are unable to access your files and receive error messages when trying to open them, this could be a sign of ransomware. - Pay attention to increased disk activity
If you notice a sudden increase in disk activity, especially if you're not running any resource-intensive applications, it could indicate ransomware encrypting files. - Be careful with pop-ups or messages
Ransomware might display warning messages or ransom notes on your screen, demanding payment to unlock your files. Don't interact with these messages.
Phishing
Phishing is the most common tactic to spread ransomware. Hackers use phishing to prompt users via e-mail to click on links, provide passwords, download files, execute macros, and install malware – which they can all exploit later. This social engineering technique can be highly targeted, with attackers gathering information about their victims from a variety of sources (e.g., social media profiles).
The recommendations for ransomware and malware also apply to phishing. Here are some additional ways employees can detect phishing attacks:
- Check the sender's e-mail address
Phishers often use e-mail addresses that mimic legitimate ones. Look closely at the e-mail address to see if it matches the official domain of the organization. Be cautious of minor misspellings or variations. - Inspect the URL
Hover your mouse pointer over any links in the e-mail (without clicking) to see the actual URL. Check if the link matches the official website's URL. Be wary of URLs that use URL shorteners or direct you to unfamiliar domains. - Avoid urgent requests
Phishers often create a sense of urgency to pressure you into taking immediate action. Be cautious of e-mails that demand quick responses, threaten account closure, or promise rewards. - Check for poor grammar and spelling
Phishing e-mails tend to contain grammatical errors, misspellings, and awkward language. Legitimate organizations usually have better quality control over their communications. - Verify requests for personal or financial information
Legitimate organizations will not ask you to provide sensitive information like passwords, credit card numbers, or social security numbers via e-mail. If you're unsure, contact the organization using official contact information rather than responding to the e-mail. - Check for generic greetings
Phishing e-mails usually use generic greetings like «Dear customer» instead of addressing you by name. Legitimate organizations typically use your name in their communications.
Exploiting vulnerabilities
Vulnerabilities are flaws in a computer system – hardware or software – that weaken the overall security of the system. By exploiting them, attackers can gain access to the system, steal data and install malware, enabling them to take full control, move to other systems, and potentially take over the whole network.
Employees play a key role in this process, as they are often the first line of defense. In addition to the recommendations above (namely be cautious with attachments, be aware of social engineering and phishing, check URLs), they can take the following steps to recognize potential attacks:
- Verify the source
If you receive a request for sensitive information or an unusual task from a colleague, supervisor, or even a higher-up, verify the request through a separate communication channel before taking any action. - Monitor network traffic
If you notice unusual network activity, such as unexpected outbound connections or large data transfers, report it to your IT/security team. - Pay attention to unusual behavior
Keep an eye out for any abnormal behavior on your computer or network, such as unauthorized software installations, sudden slowdowns, or system crashes. - Report suspicious activity
If you suspect any form of cyberattack or unauthorized access, report it to your organization's IT or security team immediately. Time is of the essence in responding to potential threats.
Cybersecurity culture success stories: 2 Swiss companies acting as role models

Proton
Swiss-based Proton provides free and open-source technology to millions of people and organizations to expand access to privacy, security, and freedom online. Their services include easy-to-use encrypted e-mail, calendar, file storage, and VPN – built on the principle of the user’s data and rules.
ProtonMail, for example, offers end-to-end encryption for e-mails, meaning only the sender and recipient can access the content of the messages. ProtonVPN aims to provide secure and private internet browsing by encrypting users' internet traffic and routing it through a network of secure servers.
In addition to strong ecryption, privacy is ensured by open-source code and Swiss privacy laws. Unlike most tech companies, Proton does not exploit user data.
![]()
Decentriq
A spin-off from the university of St.Gallen HSG, Decentriq provides a data collaboration platform with so-called data clean rooms - a neutral place where sensitive data can be combined and analyzed in encrypted form within a secure framework.
Organizations can upload encrypted datasets, defining exactly how the data should be usable and which analysis results may be shared. During the entire process, the data records remain encrypted and invisible to all other participants, including Decentriq. Consequently, full control remains with the data owner. Decentriq thus allows users of their platform to strengthen their cybersecurity.
In a project led by the Federal Office for Defence Procurement (Armasuisse), the Swiss National Bank, the Zurich Cantonal Bank, and the stock exchange service provider SIX combined highly sensitive data on phishing attacks with one another. This allowed the three financial institutions to identify threats across their organizations and compare their defence strategies. They gained valuable insights into cyberthreats without having to share sensitive data.
Your employees are your most valuable asset – more than ever
In the future, it will be even more important for companies to protect themselves against cyberattacks – due to the ongoing digitalization with modern applications, cloud computing and the IoT. If a company becomes the victim of data theft, it may even be forced out of business. The most effective lever to counter this risk is the employees. Raise their awareness of cybersecurity, give them responsibility and make them part of a well established cybersecurity culture. When all the links in the defense chain are firmly connected, attackers don't stand a chance.





