How is the threat landscape changing? Which companies are most vulnerable and how can they protect themselves against attacks? Simon Künzler, Managing Director of Kessler Consulting AG, and Tim Beutler, Delivery Manager Security Consulting of Adnovum, know the answers to these and other burning questions.
Spoiler alert: Kessler and Adnovum have joined forces and recently launched a cyber awareness training program to support Swiss companies in building awareness for cybercrime among employees and managers. This will allow companies to avoid simple, but expensive mistakes that can open doors for attackers.
1. Who are Simon and Tim?
Simon Künzler
My name is Simon Künzler, I am the Managing Director of Kessler Consulting AG, an affiliated company of Kessler & Co AG, the leading Swiss enterprise specializing in risk, insurance, and pension benefits. I am responsible for the risk management practice and a member of the leadership team of Marsh Advisory Continental Europe. Risk management is my professional passion and has been one of my focus topics since my studies. The multifaceted and constantly changing risk landscapes and their categorization with my clients in their entrepreneurial context are exciting. Current risk topics include ESG or cyber.
Tim Beutler
My name is Tim, I work at Adnovum, a company with long-standing experience in software engineering and cybersecurity. I am responsible for successfully executing our security consulting mandates, and I work on them myself. I have built up my cybersecurity knowledge in various roles in numerous projects, e.g. network security, identity and access management and security consulting.
To me, it's important to be in direct contact with clients. That's the only way I can find out about the real needs and challenges in the market.
2. How is the cybersecurity threat landscape for businesses evolving in Switzerland and internationally?
Simon Künzler
Cybersecurity is more of a global challenge than a typical Swiss issue. However, Switzerland, along with many comparable countries, is in the focus of potential attackers because it is known as a rich and internationally highly interconnected economy. Last but not least, based on the reported cyber claims, we see that the cyber threat continues to grow. According to a report published by Marsh in October 2022, cyber claims increased by 37% in continental Europe alone between 2020 and 2021. Other studies also indicate that, contrary to recent years, attackers are no longer focusing solely on Europe, the USA, or international financial centers, but are increasingly targeting regions of the world such as Asia, Africa, and South America.
Tim Beutler
The continuing digitalization in the business and private world makes cyberattacks increasingly attractive. The motives behind this do not always have to be of a financial nature. When we look at current conflicts around the world, we see that cyberattacks have become part of the standard repertoire of modern warfare.
3. What are the most common forms of cyberattacks against companies? How do they work?
Tim Beutler
The most common one is blackmail. The reasons are varied, which illustrates the risk exposure. Typical gateways are malware attacks or so-called social engineering attacks. The latter include phishing, vishing, or smishing. Attackers use phishing e-mails to gain access to companies, where they later introduce ransomware. They use it to encrypt data, including backups if possible, and ask for a ransom to unblock it.
4. What are the most common consequences of a successful cyberattack on businesses?
Simon Künzler
It depends on the kind of attack and the IT and OT systems concerned. In the event of a successful ransomware attack, a company is unable to access its data and systems, which results in a business interruption – the most severe impact. Such an interruption can last several days, the «recovery work» may take weeks or even months. Even worse: a data leakage, especially if it becomes known, threatens to cause lasting damage to the company's reputation. If the data leakage qualifies as a data breach, fines and other legal consequences are possible. In the worst case, such an attack threatens the existence of the company.
5. What is the most impressive cybersecurity attack on a business we’ve seen in the media over the last couple of years and how could it have been prevented?
Tim Beutler
There have been several devastating attacks in the past. The most notable one was WannaCry. The computer virus appeared over five years ago as ransomware and encrypted all data on infected Windows operating systems. The data was only unlocked for a ransom paid in Bitcoin. WannaCry affected both business and private users. What was special about it was how incredibly fast it spread. Those who had patched their systems in time were not affected.
Also notable was a May 2021 ransomware attack on Colonial Pipeline, an American oil pipeline company in the western United States. It clearly showed us how vulnerable supply chains are. Even flight schedules at the nearby airport had to be adjusted due to the fuel shortage resulting from the disrupted supply chain.
6. How are cyberthreats different for small and large businesses and who is more at risk?
Simon Künzler
Thinking that smaller or medium-sized companies are unattractive to attackers is a fallacy. They tend to be even more vulnerable. They are less aware, have less cyber-specific expertise and less budget for cyber prevention than larger companies. But even the big players are not spared. For an attacker, the ultimate question is always one of effort versus return. The goal is to achieve the highest possible financial gain.
There are actually differences between the industries. A preferred target is and remains the financial sector, where reputation is the primary concern. Imagine your bank is hacked – the loss of trust is enormous. Another target is the manufacturing industry, whose operating technology is often less mature than that of financial institutions. Successful cyberattacks against manufacturers and the industrial control systems have physical implications and severely disrupt production.
7. How can employees unconsciously open doors for hackers?
Simon Künzler
I always find that the weakest link in the chain of defense is the human being. When dealing with e-mails, their attachments, and links, as well as when providing information by telephone, special caution is required.
Tim Beutler
Individuals in a company who are not careful can still facilitate an attack. They may unintentionally disclose information in conversations or e-mails or fail to recognize phishing e-mails as such. It is even worse when IT professionals neglect their duty of care, for example by not patching systems regularly. A security culture in which mistakes are openly discussed and an awareness for IT security is created can ease this problem.
8. How can companies prevent and recover from cyberattacks?
Tim Beutler
First, there needs to be an understanding of cyber security within the company and support from the management. In practical terms, this also means a budget and sufficient resources. In addition, suitable organizational structures and processes are required. This is referred to as an information security management system (ISMS).
In addition to technical measures, an ISMS also includes the management of supplier relationships and emergency plans for extraordinary incidents. A real security culture is also helpful, i.e. employees must be trained.
If, nonetheless, an incident should occur, it depends on its severity and the measures in place as to how quickly normal operation can be restored. In the worst case, the system comes to a complete halt and must be restarted with backups. Then it is important that the emergency plan not only exists on paper, but also in the minds of the employees. First, it is essential to know which systems are affected and to limit the damage. The systems are disconnected from the network, and it is advisable to initiate a forensic investigation. Furthermore, a report should be sent to the NCSC and legal steps should be taken.
9. How does a cyber risk awareness training work? Whom is it for?
Simon Künzler
The training is primarily aimed at companies that attach great importance to cybersecurity culture. It is suitable for managers as well as for all employees with system access.
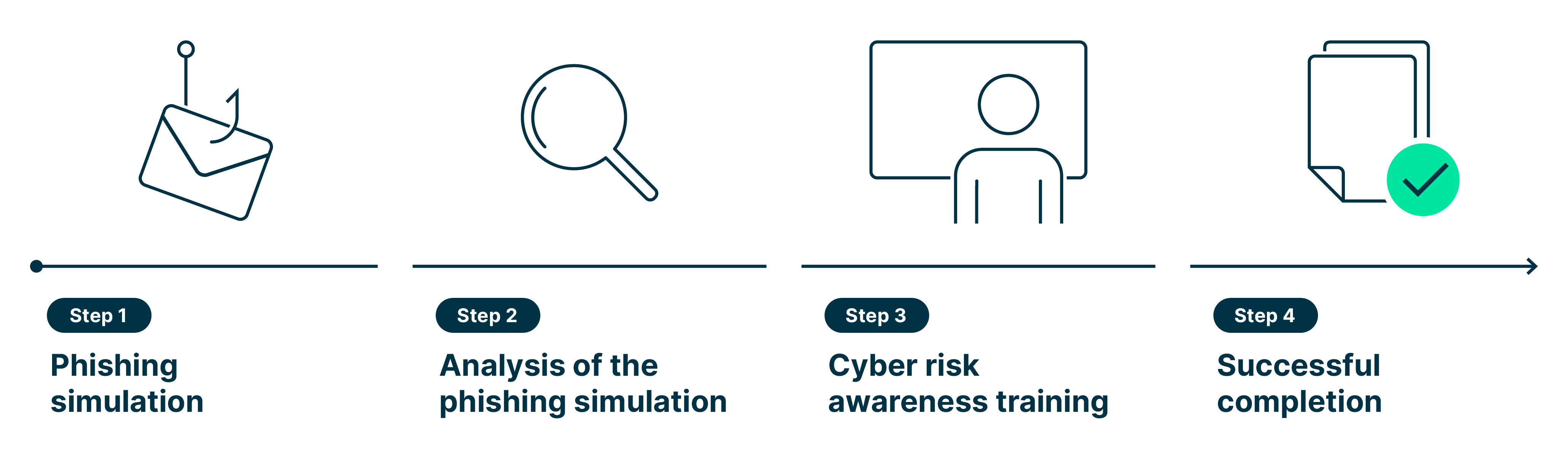
Ideally, the training takes the form of an interactive workshop that demonstrates the threat situation and defines rules of conduct for dealing with cyber issues. On the one hand, the aim is to impart basic knowledge about attack patterns, and on the other hand, to discuss the company's specific cyber exposure in order to strengthen the responsible use of information and communication technologies. Prior to the training, a phishing campaign is carried out to assess and raise employees' awareness.
10. Tell us a fact on cyber risk most people don’t know about.
Simon Künzler
Today, we find that dependency on network, system, platform, or application suppliers is not yet sufficiently on our clients' radar. In the interconnected world we live in, we and companies are just as protected as the weakest link in their supply or value chain.
Tim Beutler
Perhaps that the word «cyber» originates from the Greek and means «control». Today it is considered to be short for cybernetics, which describes the science of control and regulation processes.
In general, «cyber» is now associated with computers, e.g. cyberspace for a world generated by computers or cyber risk for computer-specific risks.






