«Assets» include anything that is relevant to a specific business purpose in a particular context and therefore essential for survival. Therefore, it is key to protect the assets to ensure their confidentiality, integrity and availability.
What is considered an «asset», however, is a question of perspective: For a company manager, an asset is, for example, established customer trust, for the cybersecurity specialist it is the IT systems, for the information security officer it is information of all kinds, and for the data privacy officer it is personal data.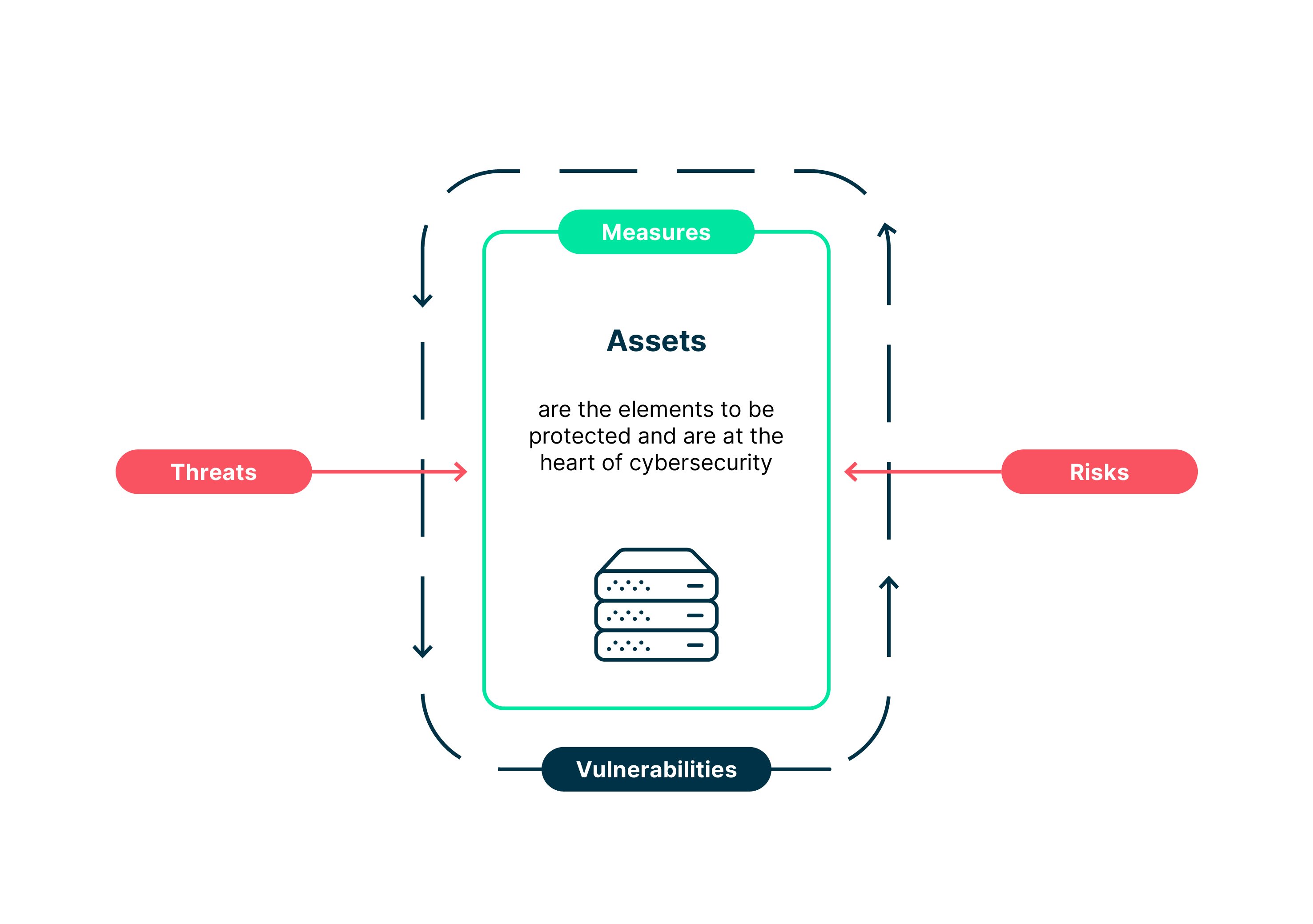
Knowing one’s assets – why is it so important?
Only if you know and understand the assets you want to protect, you will be able to assess and manage your risks. Unfortunately, there is little practical guidance on how to collect assets so that they are fully mapped and changes can be quickly identified.
Identifying assets in everyday life
Usually, assets are collected in close and regular collaboration with those responsible for applications and specialist areas in the company.
Many information security managers are unhappy with this, as they believe they cannot rely on the completeness and timeliness of the assets documented in this way. In fact, most companies do not know in detail which systems, information and data they have where and in which processes which data is used.
Even inventory solutions often only serve to provide transparency per se, are based on a very limited understanding of «assets» or are unsuitable for putting assets into a corporate risk context and deriving protective measures.
Principles and challenges
For assets to be useful as a basis for risk analysis, it is crucial to determine them systematically and to observe the following principles:
- Capture assets in a granular and detailed way so as not to miss valuable components
- Describe assets as what needs to be protected rather than reducing them to their attack surface
- Include assets that cannot be derived from process descriptions
- Try to detect changes in the asset and system landscape at an early stage
Identify assets in a targeted manner for a solid cybersecurity foundation
For the most complete and up-to-date determination of assets, a combination of different approaches is recommended:
- Start from the IAM solutions and derive what the people or devices managed in them can access
- Start from all inventories and merge this information about assets
- Start from existing documentation of the system landscape, network structure, IT architectures and processes
- Start from the knowledge of the process and application managers
- Start from the real data traffic to understand which systems and assets are accessed
Clearly, identifying assets requires a wide range of expertise, experience and resources – which is often lacking within the company. However, the money would be well invested here, as cybersecurity has moved from being a pure IT issue to an urgent business issue.
---
This article was published in Netzwoche on August 24, 2022







