- On this page
- What is Self-Sovereign Identity?
- What is Digital Identity and what does «self-sovereign identity» mean?
- The principles of Self-Sovereign Identity in a digital world
- New vs old: What changes for the user with SSI?
- SSI: typical use cases
- Self-Sovereign Identity in Switzerland
- The future of Self-Sovereign Identity
- E-ID and SSI are the next steps of digitalization in Switzerland
- FAQ
- SSI Glossary (terms explained)
Self-Sovereign Identity is the next level of digital identity. It comes with unparalleled benefits for both organizations and users. We show you what they are, how Self-Sovereign Identity works and how it will impact our lives.
According to McKinsey Global Institute research, extending full digital ID and SSI coverage in countries including the US and the UK could unlock economic value equivalent to 3 to 13% of GDP in 2030.
Nevertheless, in Switzerland, for example, citizens rejected the e-ID Act in a referendum in March 2021. Of the 2’762’770 individuals who voted (voter turnout of 51.29%) 64.4% said «no», and only 35.6% said «yes».
Learning from the reasons of rejection Switzerland initiates the next E-ID law with higher privacy and higher responsibility by government. Hence, Switzerland is among the major players of the SSI movement.
In this blog post, we will explore the concept of SSI, its benefits, and the current legislation in Switzerland. We will provide background information on its evolution, the underlying principles and potential impact across industries.
At the end, you will have a comprehensive understanding of SSI, its potential in Switzerland, and how it can revolutionize the way we interact with our digital identities.
What is Self-Sovereign Identity?
Self-Sovereign Identity (SSI) is a forward-looking concept that is gaining popularity in the digital world. It provides individuals with control over their personal data by allowing them to conveniently and securely store the data in their mobile wallet.
What is Digital Identity and what does «self-sovereign identity» mean?
The concept of digital identity
Identity literally means the quality of being identical – to yourself. Cambridge dictionary defines identity as «a person's name and other facts about who they are».
A digital identity is the information and data that identifies an individual in the digital world. It consists of a set of digitally captured attributes, such as name, date of birth, and gender combined with credentials that are linked to a unique identifier.
In other words: An electronic representation of a person often used to access online services, make purchases, and interact with others on digital platforms. A digital identity can include personal information as well as a person's online behavior.
What does «self-sovereign identity» mean?
«Self-Sovereign Identity» or «SSI» refers to a decentralized approach where individuals do not rely on a third-party provider. They can store their identity information securely on their personal device using cryptographic techniques. Plus, they can selectively disclose personal data to trusted entities or service providers.
SSI thus addresses the privacy and security concerns associated with traditional identity systems, where personal information is often stored in centralized databases vulnerable to breaches and misuses.
Why is digital identity important?
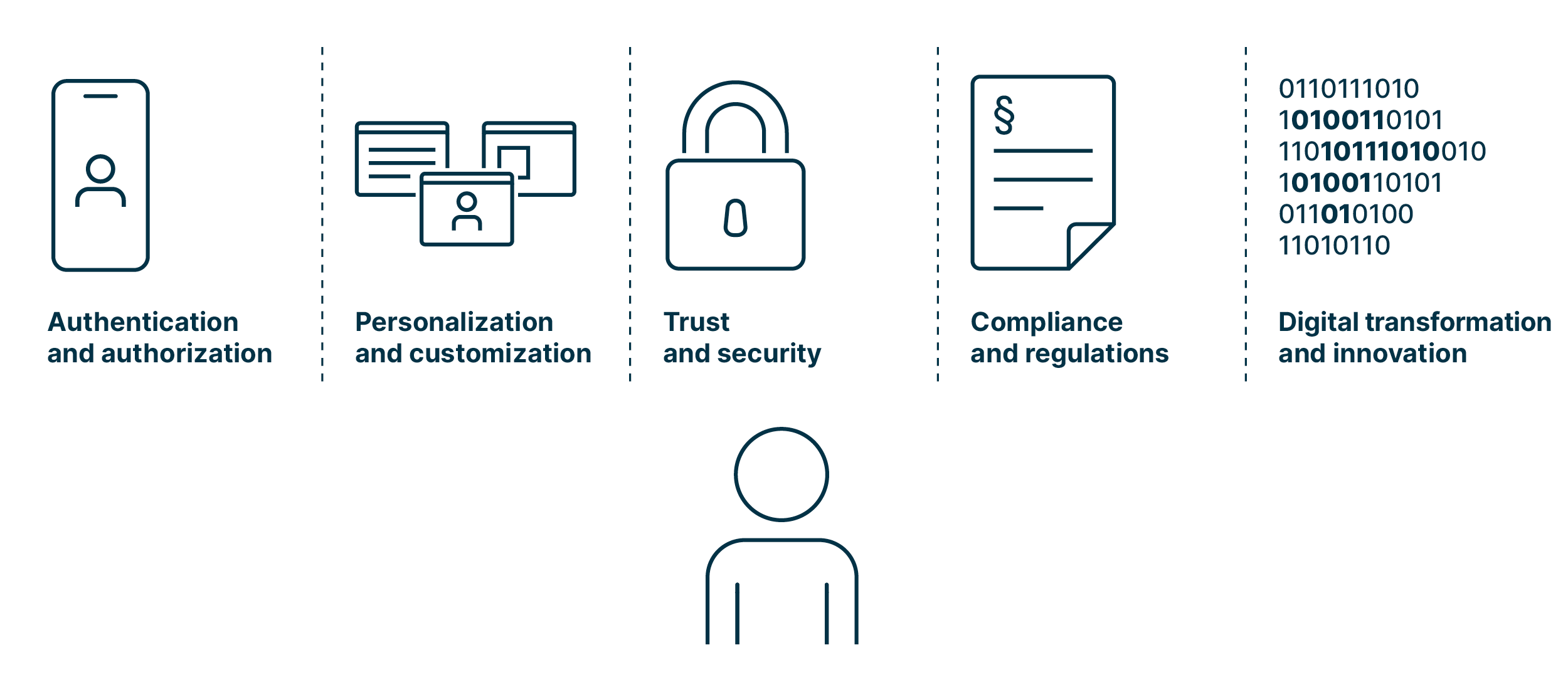
Digitalization requires digital identity for a number of good reasons:
-
Authentication and authorization
Digital identity provides a way to authenticate and authorize individuals, organizations, or devices in the digital realm. It ensures that the right people or entities have access to the appropriate resources, services, or information.
-
Personalization and customization
Digital identities allow for personalized user experiences in the digital world when an individual opts for it. By associating digital identities with individuals, organizations can tailor services, content, and recommendations based on their preferences, behavior, and historical data.
-
Trust and security
Digital identities play a crucial role in establishing trust and ensuring security in digital interactions. By verifying the identity of participants, digital identity systems help prevent fraud, identity theft, and other malicious activities, thus enabling secure communication, data exchange, and transactions.
-
Compliance and regulations
Digital identity is key for compliance with legal and regulatory requirements. Many jurisdictions have implemented data protection and privacy regulations that require the identification and verification of individuals in digital transactions. Digital identity systems can help organizations establish accountability for data handling and protection.
-
Digital transformation and innovation
Digital identity is a cornerstone of digital transformation initiatives. It enables organizations to transition from paper-based processes to digital workflows, thus opening doors for new business models, such as sharing economy platforms, and fostering innovation and economic growth.
|
«Although invisible to users, SSI allows organizations to minimize personal data storage and preserve the privacy of individuals, while bringing them faster and cheaper integration with civil and employee IDs.» Hans Burger |
|
Taking responsibility - individuals need to be aware of whom to trust
While a digital identity is a convenient means of authentication for individuals, it also provides a wealth of information to service providers, including a person’s thoughts, needs and actions.
It is therefore essential for individuals to understand how sensitive the information contained in a digital identity is. Plus, what action is performed in which moment, what evidence of this is in a system, and what can happen in case of data loss or data theft.
Another fact individuals need to be aware of: It is hard to align our requirements – having complete control of our data – with our expectations – having a third party validate our identity.
In Switzerland, the discussion about digital identities is shifting from the technical to the political area as the government enacted a new data protection law on 1 September 2023. Chances are that the political discussion will help to reach a broader audience and result in a decent level of digital literacy of citizens. However, the government will have to put a lot of effort into it and even convince young people, i.e., digital natives, of the benefits of E-ID.
The evolution of SSI
Since the World Wide Web (WWW) was released in August 1991, the way we prove our identity has considerably changed. Let us take a walk down memory lane, starting with physical IDs:
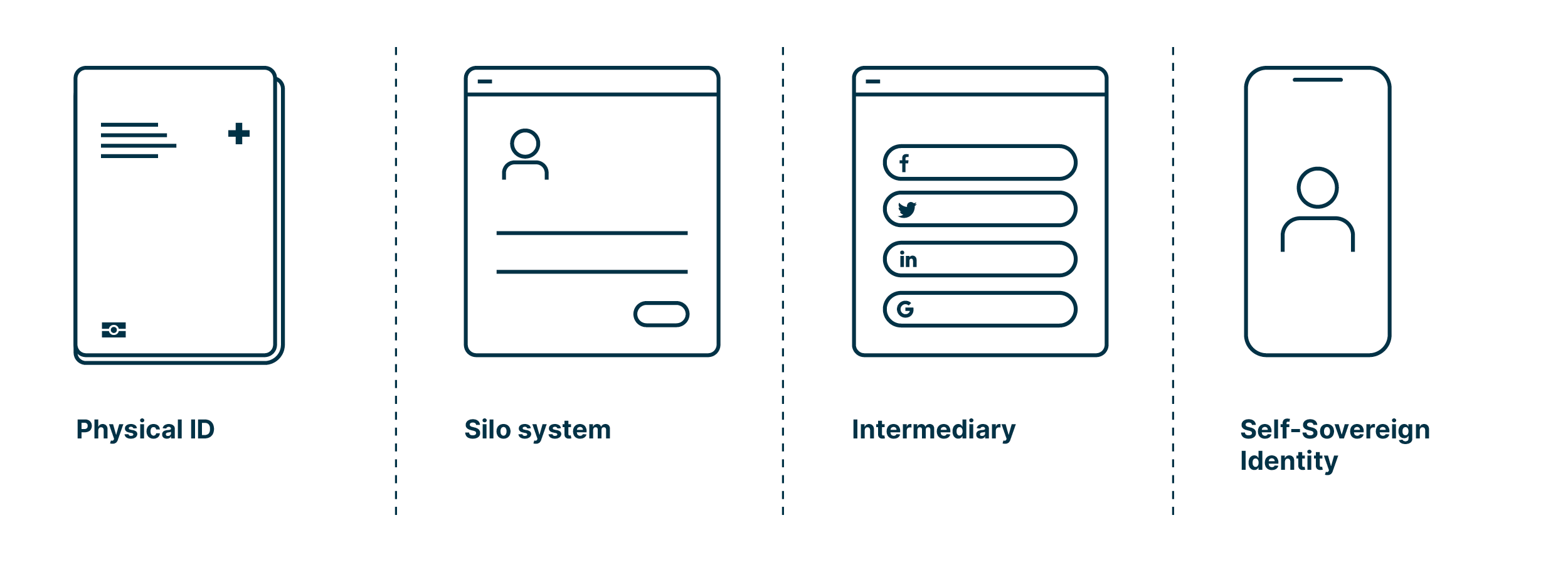
In the traditionally used physical proofs of identity, such as passports, the focus was and is on trust in the issuer. This trust is ensured by security features:
- The higher the value of a document, the greater the effort put into the security features.
- In recent years, biometric information has been integrated into physical documents in addition to passwords and codes.
- The physical proofs of identity work because the verifying party (e.g., customs or a merchant) trusts the issuing party (e.g., municipality for ID or bank for bank card).
Once the World Wide Web went live, the need for electronic identities started to emerge. The early days were characterized by the internet of «silo systems»:
- The internet only knows the servers’ identities.
- The users’ identities were never integrated into the concept or protocol.
- This resulted in specific identities and logins for every application or service, since each service assigned its own passwords and verified the identity differently or from scratch.
- This led to silos where e-mail addresses or proper user names identify the users, and passwords serve as credential.
Then «intermediaries» entered the scene, whose approach promised a way out of the password chaos:
- Intermediaries are known as social identity providers (IdP).
- Often, powerful internet companies provide this service. This central approach comes with certain problems:
- The identity data is held by these IdPs and is often used for other purposes as well.
- The IdPs can deny access or exclude users.
- The IdPs are aware of the sites individuals access using their credentials.
- The user must trust the IdP, even if it has no official legitimation.
Today «Self-Sovereign Identity» finally gives individuals back control of their data:
- Self-Sovereign Identity is comparable to the physical identity:
- The user keeps the information with him, just as an ID in his wallet.
- The issuing party cryptographically confirms the data, just like a certification.
- The verifying party trusts the issuing party.
- Thanks to the decentralized approach, the user is independent from a central issuing and managing party.
The principles of Self-Sovereign Identity in a digital world
How does the digital world work?
The digital world allows fully leveraging the potential of Self-Sovereign Identity as the involved parties are connected in a trusted environment. Actors include the holder, the issuer and the verifier.
The issuer is an institution that distributes verifiable credentials* (VC), such as an authority issuing an identity, an insurance issuing a health card or a university issuing a diploma. The holder is the person in the center of the system and stores the verifiable credentials, such as identity, certificates, or home address, in their mobile wallet, which is the core of Self-Sovereign Identity. The verifier is a service provider who authenticates the holder before granting him access to the offering.
The following diagram illustrates how issuer, holder, and verifier interact:
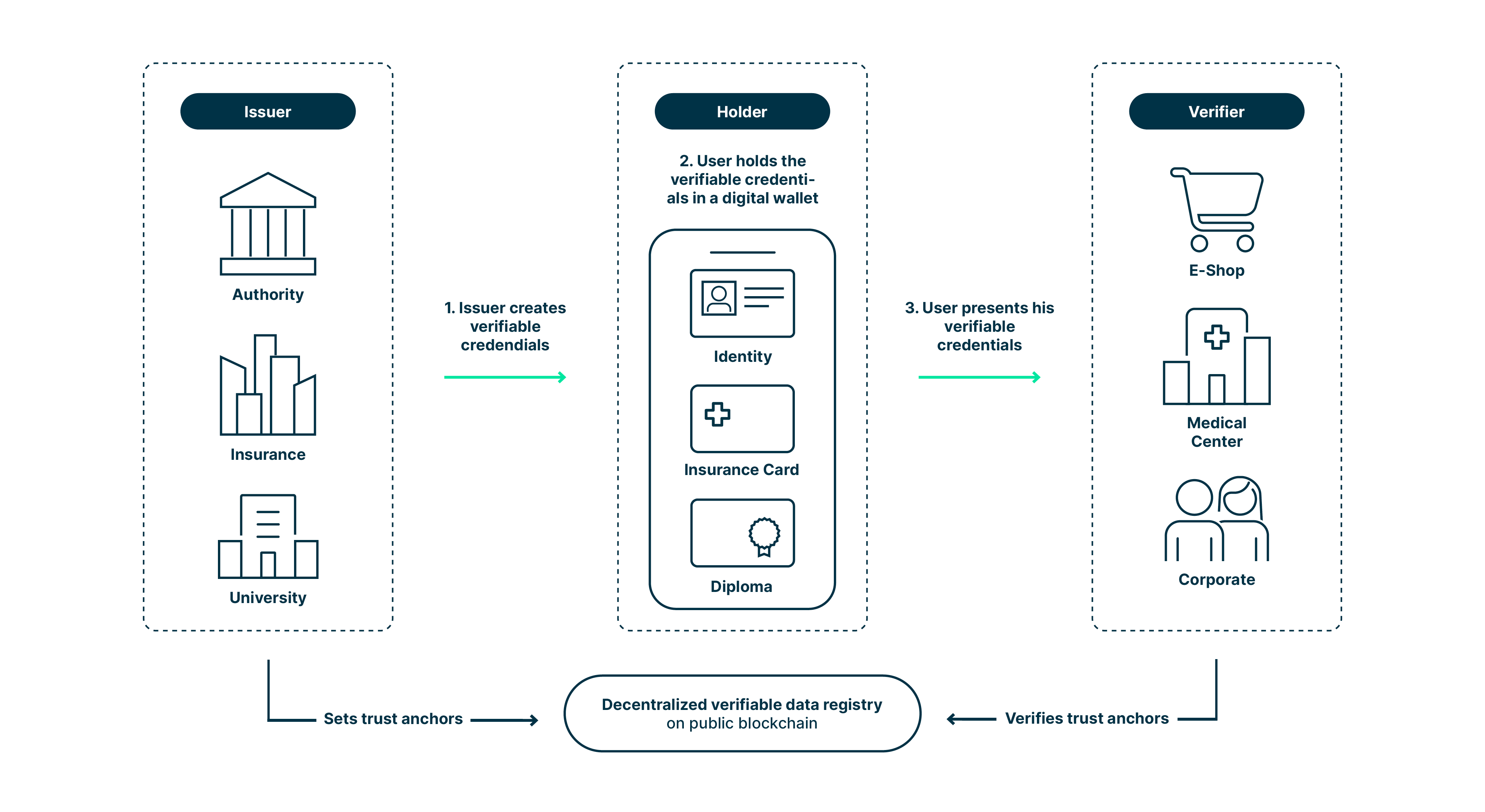
We like to think of the digital world as an ecosystem, i.e. a distributed, adaptive, open system with properties of self-organization, scalability and sustainability inspired from natural ecosystems.
*Verifiable credentials according to W3C:
«A verifiable credential can represent all of the same information as a physical credential. The addition of technologies, such as digital signatures, makes verifiable credentials more tamper-evident and more trustworthy than their physical counterparts.»
What are the ten guiding principles of Self-Sovereign Identity?

There is no clear consensus on what SSI is among different thought leaders and organizations. However, the following 10 key principles summarize the essential aspects of SSI:
- Existence
A user must be able to exist in the digital world and to trust specific third-party providers, i.e., issuers who have gathered the necessary authority to establish trust amongst verifiers. - Control
Individuals must have ultimate authority over their digital identities and personal data. - Access
Users must have easy and direct access to their own data. - Transparency
The way an identity system and algorithms are managed and updated must be publicly available and reasonably understandable. The solution design should be based on open protocol standards and open software. - Persistence
Identities must be long-lasting. Solution developers should implement sufficient foundational infrastructure and design sustainable commercial and operational models. - Portability
Individuals must be able to bring their identities and credentials anywhere, transport their data from one platform to another, and not be restricted to a single platform. - Interoperability
Identities should be as widely usable as possible by various stakeholders. Organizations, databases, and registries must be able to quickly and efficiently communicate with each other globally through a digital identity system. - Consent
Users must give explicit permission for an entity to use or access their data. The process of expressing consent should be interactive and well-understood by individuals. - Minimization
A digital identity solution should enable individuals to share the least possible amount of data that another party needs to avoid sharing of unnecessary personally identifiable information. - Protection
Individuals’ right to privacy must be protected and safeguards should exist against tampering and monitoring information. Data traffic should be encrypted end-to-end.
New vs old: What changes for the user with Self-Sovereign Identity?
Old and current personal identification (ID)
Most people today use federated identities, which link an individual’s electronic identity to attributes and are stored across multiple identity management systems. Thanks to single sign-on (SSO), which relates to authentication within a federated identity management system, a user logs in only once and is trusted across multiple IT systems or organizations. One example is Google login.
Passports have developed from a purely physical to a hybrid means of identification, as in recent years biometric information has been integrated in addition to passwords and codes.
Federated identities and passports have one thing in common: The individuals’ data is stored centrally by the IdP on their system, everyone else must interact with it.
This is exactly where SSI with its decentralized approach and mobile wallet kicks in.

New: Gain control of personal data with Self-Sovereign Identity and mobile wallets
Mobile wallets are the primary differentiating factor of SSI. Thanks to them, SSI solves core privacy problems of centralized and federated identity models and offers new ways of using identities and official documents.
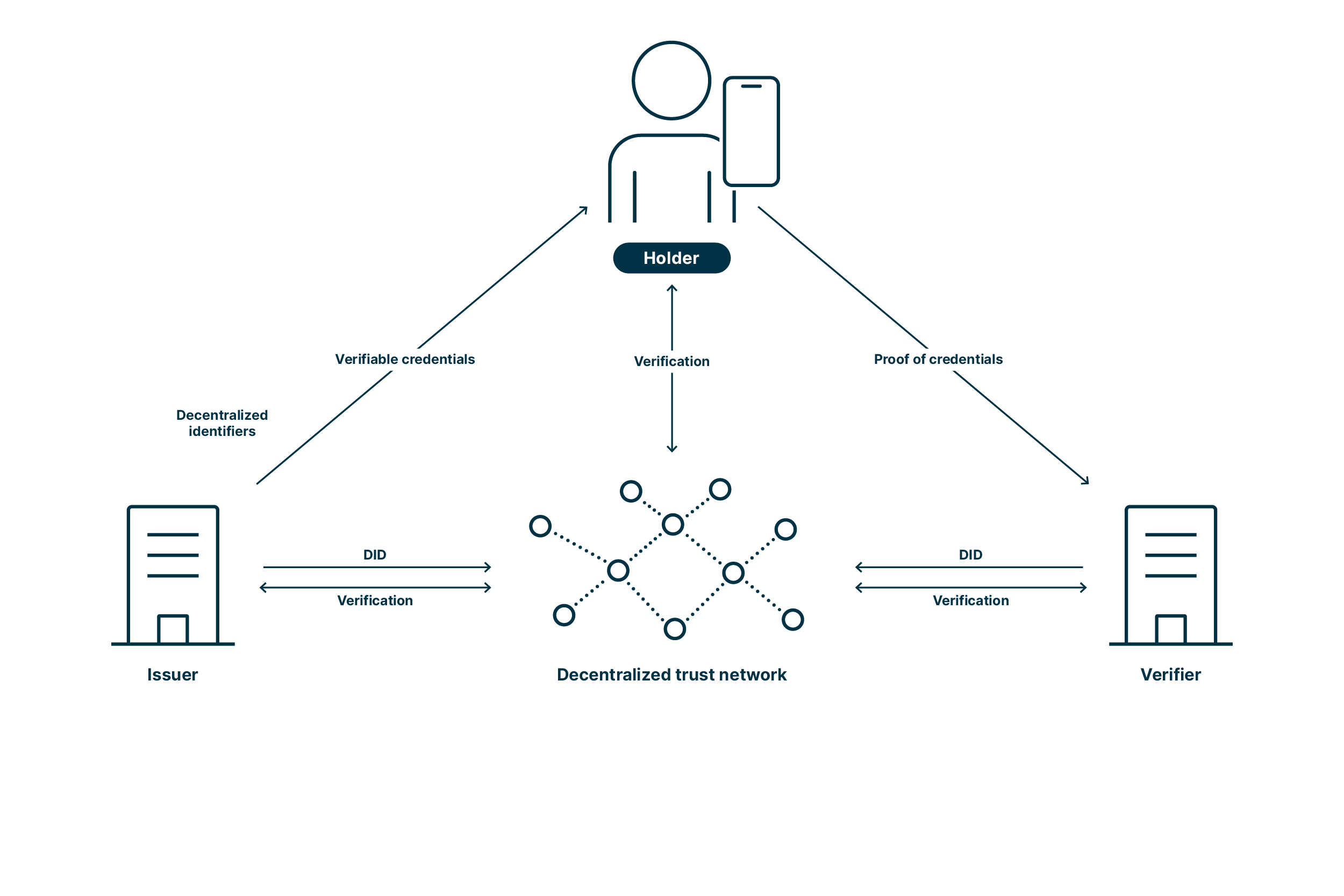
This is made possible by verifiable credentials and decentralized identifiers (DID). Verified credentials refer to digital representations of personal information or qualifications that have been issued by a trusted authority and can be verified independently. Decentralized identifiers are a form of unique digital identifiers that are independent of any central authority.
The benefits of Self-Sovereign Identity for every role in today’s digital world
As holders, users have full control of their personal data which are stored in their mobile wallet. Using their wallet, they keep their credentials and authentication activities confidential. SSI also gives them the possibility to disclose information selectively (only the minimum amount of data necessary to accomplish the task at hand). Additionally, they benefit from zero-knowledge proofs (ZKP). ZKP allows a holder to answer a yes-or-no question without revealing the data. The most common example is proving that the holder is over 18 without disclosing his birthday.
By using SSI, the issuer can easily create credentials and prevent fraud, because via cryptography the issued verifiable credential is ensured to be immutable.
Just as the holder, the verifier also benefits from data privacy. Thanks to ZKP, it is possible to verify information without getting the data. This allows easier compliance with the data privacy laws GPDR and FADP. Plus, SSI enables a secure and easy verification of the issued credentials in both the virtual and the physical world.
Self-Sovereign Identity: data flow from issuer to verifier
The following picture illustrates the workflow between issuer, verifier, and holder:
The difference for the user with Self-Sovereign Identity in a nutshell
|
|
E-ID based on federated identity |
E-ID based on Self-Sovereign Identity |
|
Data privacy |
Data stored with issuer |
Data stored in individual’s mobile wallet |
|
Independence |
Individual relies on a central authority for verification |
Individual provides information directly to service provider who acts as verifier |
|
Flexibility |
Individual has to provide the information requested by the verifier |
Individual has full control of data and can disclose information selectively, even answer yes-or-no questions |
Self-Sovereign Identity and mobile wallets in the real world
SSI is not limited to the digital universe, but could also be applied in the real world – in a much simpler way.
Self-Sovereign Identity has the potential to replace physical forms of identification, such as student cards or passports. This would mean much more than simply swapping existing physical solutions for a digital counterpart. The major benefit: Also in the real world, SSI comes with selective information sharing and ZKP.
The challenge lies in the verification process. In the digital world, the workflow is initiated by the verifier, starting a back-and-forth between him and the holder. Real-world interactions require a more straightforward way, i.e., a user-initiated process:
- The user initiates the process by opening their mobile wallet and presenting a QR code
- The verifier scans this code to open a private and secure channel between the two parties
- The verifier uses this channel to receive and check the relevant information from a verifiable credential
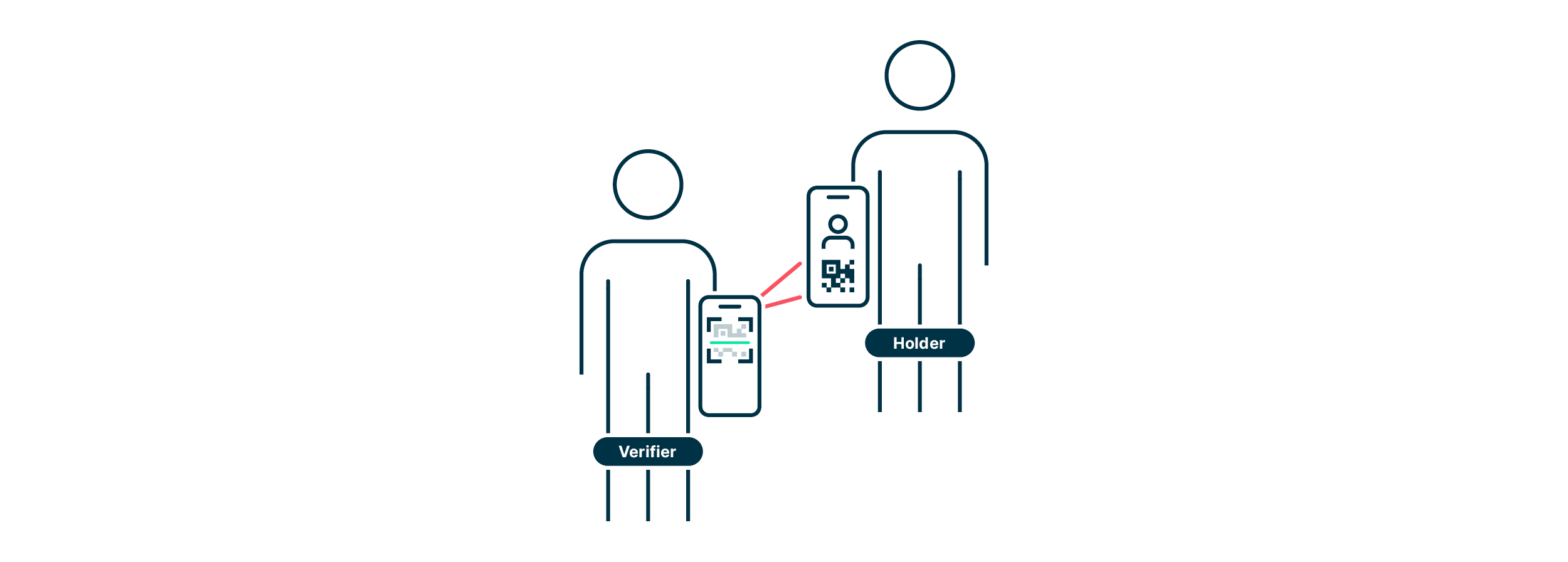
One key decision would be to use edge mobile wallets, since using hosted wallets invalidates many of the advantages highlighted above by centralizing information. Using edge wallets also offers the advantage of making peer-to-peer (or offline) connections possible in the future (e.g., over Bluetooth). This would eventually allow for the adoption of SSI in a wider range of real-world scenarios.
Self-Sovereign Identity: typical use cases
There is no better way to understand a new technology and assess its potential added value than with representative use cases.
Examples of use cases across industries
- Education
Alice stores her educational achievements in her digital wallet and shares them with educational institutions, for example when applying for a university or registering for an exam. The university uses SSI to manage and verify Alice’s and other students’ academic credentials, certifications, and diplomas. - Finance
When Bill needs to carry out online transactions, he uses his verifiable credentials to log in to his account. The bank also accepted his VCs for initial onboarding as a client instead of a more time-consuming video identification. - Healthcare
Cindy needs to see a dentist for a routine job. Therefore, she does not want to provide her complete medical record, but only the specific information the dentist needs. Also here, SSI ensures privacy. - Travel
Daniel is enjoying his vacation to the max. Thanks to SSI and his verifiable and tamper-proof digital identity, he passes the airport security checks and immigration process faster than ever before. Plus, as a rather absent-minded fellow, he doesn’t need to bother about losing his physical documents. - Legal services
Esther and her husband have just bought a new home and now need to sign the purchase contract. SSI enables them to digitally sign the document with cryptographic proofs of their identity.
Obviously, the potential of SSI should not be underestimated. According to McKinsey Global Institute research, SSI could be key to unlocking access to banking, government benefits, education, and many other services. Research suggests it could boost economic growth by 3% in the UK in 2030. Similar numbers can be expected for other countries.
Self-Sovereign Identity in Switzerland
The upcoming E-ID Act will open the door for the introduction of a nationwide E-ID in Switzerland. The Swiss Federal government will act as issuer and operate the infrastructure. To give citizens complete control over their data, the E-ID is based on SSI.
Voting against E-ID in 2021 and beyond
- March 2021
Swiss citizens reject the E-ID Act. The Swiss Federal government therefore works at full speed on a new proposal. - September 2021
The Federal government publishes the first results in a discussion paper. Self-sovereign identity is one of three possible solutions proposed for the implementation of the future E-ID. - December 2021
The Federal government defines the design principles of the future government-issued E-ID which should give users the greatest possible control over their data. - June 2022
The draft of the new E-ID law goes out for consultation. - March 2023
The Public Sandbox Test Infrastructure goes live. - June 2023
The Swiss government shifts their main focus from SSI to compatibility with the EU solution. - September 2023
The revised Federal Act on Data Protection (revFADP) – aiming to better protect Swiss citizens' data – entered into force on September 1 and may lay the grounds for the adoption of the E-ID.
The future of Self-Sovereign Identity
SSI has the potential to reshape digital identity. However, its widespread adoption and realization of its full potential will depend on various factors, including technological advancements, acceptance by society, market demand, and regulatory developments.
Drivers of Self-Sovereign Identity
The following factors drive the development and adoption of self-sovereign identity:
- Privacy and data protection
Individuals are becoming more concerned about the privacy and security of their personal data. SSI provides a way to maintain control over one's identity information, reducing the risk of data breaches and unauthorized access by minimizing the reliance on centralized databases. - Security and trust
Centralized identity systems are susceptible to hacking and identity theft. SSI utilizes cryptographic techniques and decentralized networks, such as blockchain, to enhance security and build trust by ensuring that identity data is tamper-proof and verifiable. - User-centric approach
SSI places the individual at the center of the identity management process, enabling them to decide which aspects of their identity to share and with whom. It allows individuals to create portable identities that can be used across various contexts and platforms, fostering convenience and user autonomy. - Interoperability and portability
Traditional identity systems often lack interoperability, making it challenging to use identities across different organizations and services. SSI enables this by promoting open standards and protocols, reducing redundancy and simplifying identity verification processes. - Digital inclusion
Self-sovereign identity may enable individuals who lack traditional forms of identification, such as refugees or marginalized populations, to access essential services and participate in the digital economy by providing them with a means to assert their identity in a trusted manner. - Compliance with regulations
Various regulations, such as the EU General Data Protection Regulation (GDPR), emphasize individual data rights and consent. SSI aligns with these regulations by providing individuals with greater control over their personal data, facilitating compliance with privacy and consent requirements. - Business and economic benefits
SSI can offer cost savings for organizations by reducing the need for identity verification processes, data storage, and compliance with complex identity regulations. It can also enable new business models, such as identity-based services and decentralized applications, leading to innovation and economic growth.
E-ID and Self-Sovereign Identity are the next steps of digitalization in Switzerland
You now understand the concept of SSI and its benefits: more privacy and control over data for individuals, more efficiency and easier compliance for organizations. Plus, you are familiar with the progress of SSI in Switzerland. Most important: You are aware of the impact SSI will have on numerous areas of our lives.
The new Swiss data protection law that took effect on 1 September 2023 will pave the way for the nation-wide rollout of an electronic identity. From there, SSI is only a few steps away.
FAQ
What is SSI?
SSI is a decentralized approach where individuals do not rely on a third-party provider. They can store their identity information securely on their personal device using cryptographic techniques.
How does SSI work?
The holder is the person in the center of the digital world who requests a verifiable credential – e.g., an identity or diploma – from an issuer, usually an institution. He/She then stores this credential in his/her mobile wallet, which is the core of SSI, and presents it to the verifier when authenticating to use a digital service.
What are the user benefits of SSI?
Users have full control of their personal data and keep their credentials and authentication activities confidential, as the data is stored in the wallet on their smartphone. SSI allows users to disclose information selectively or even answer a yes-or-no questions.
Where in real life can SSI be applied?
SSI can be applied in any real-life scenario requiring identity verification and authentication, e.g., to access government services such as voting or applying for a new passport, to have control over one’s medical record, to register for a university exam, or to digitally sign a contract.
How is SSI related to blockchain?
With SSI, public identifiers of an identity can be stored on a blockchain. While a blockchain is not required for SSI, it is a common implementation as it supports the principles of SSI, such as decentralization, immutability, and security.
SSI Glossary (terms explained)
|
Artificial Intelligence (AI) |
AI is the emulation of processes and capabilities of human consciousness, most commonly by computers. With various technologies and techniques ranging from machine learning (ML) to natural language processing (NLP), AI systems can analyze data, make decisions, generate natural language, and perform other tasks that previously required and were exclusively associated with human intelligence. |
|
Digital product engineering (DPE) |
The information that identifies an individual in the digital world, i.e., an electronic representation of an individual often used to access online services, make purchases, and interact with others. |
|
Generative AI |
Decentralized identifiers are globally unique identifiers made up of a string of letters and numbers that act like an identifying address on a blockchain and independent of any organization. |
|
European Blockchain Services Infrastructure (EBSI) |
EBSI is a blockchain-based infrastructure developed by the EU to provide secure and trusted services and support the implementation of SSI principles. |
|
electronic Identification, Authentication, and Trust Services (eIDAS) |
The eIDAS Regulation’s legal framework for electronic identification and trust services within the EU. It promotes cross-border recognition of electronic identities and supports secure electronic transactions. |
|
Holder |
The holder is the person in the center of the digital world who requests verifiable credentials from institutions and presents them to a verifier to access an online service. |
|
Identity provider (IdP) |
An IdP manages the subscriber’s primary authentication credentials and issues assertions derived from those credentials. |
|
Issuer |
The issuer is the party in the digital world that issues verifiable credentials. It is usually an institution, e.g., an authority, an insurer or a university. |
|
Least Privileged Access (LPA) |
LPA is a security concept that refers to the idea of limiting user access rights or permissions to the minimum required to perform necessary tasks. |
|
Level of Assurance (LoA) |
LoA refers to the degree of confidence in the claimed identity of a person: how certain a service provider can be that the person using a specific E-ID to authenticate is the person they pretend to be. |
|
Mobile wallet |
A mobile wallet enables users to securely store digital versions of payment methods, i.e., credit and debit cards or cryptocurrency, but also documents like a driver’s licence, to use on the go with their smartphones. |
|
Relying party |
A party that relies on the security and authenticity of a key or key pair for applying cryptographic protection and removing or verifying the protection that has been applied. |
|
Self-Sovereign Identity (SSI) |
SSI refers to a decentralized approach where individuals do not rely on a third-party provider and can store their identity information securely on their personal device. |
|
Selective disclosure |
Holder discloses only specific data. |
|
Verifiable credential (VC) |
A verifiable credential is a tamper-evident credential that has authorship that can be cryptographically verified. |
|
Verifier |
The verifier requests the verifiable credentials from the holder for authentication before granting the holder access to services. |
|
Zero-Knowledge Proof (ZKP) |
Holder can answer a question with yes or no. |





